SECCON2016取证题WriteUP
取证100
给了一个文件,提示是内存取证,使用volatility分析。
题目描述是找出假的svchost进程访问的页面,那么先看看svchost都有几个。
# lightless @ lightless-pc in ~/Desktop/seccon2016/volatility_2.5.linux.standalone [22:14:24]
$ ./volatility_2.5_linux_x64 -f ../forensic_100.raw filescan | grep svchost
Volatility Foundation Volatility Framework 2.5
0x000000000201ef90 1 0 R--rw- \Device\HarddiskVolume1\WINDOWS\system32\svchost.exe
0x00000000020f0268 1 0 R--r-d \Device\HarddiskVolume1\WINDOWS\svchost.exe
0x00000000024a7a90 1 0 R--rwd \Device\HarddiskVolume1\WINDOWS\system32\svchost.exe
明显第二个在WIndows目录下的svchost.exe是假的,然后把这个文件dump出来看看。
# lightless @ lightless-pc in ~/Desktop/seccon2016/volatility_2.5.linux.standalone [22:15:11]
$ ./volatility_2.5_linux_x64 -f ../forensic_100.raw dumpfiles -D output -Q 0x00000000020f0268
Volatility Foundation Volatility Framework 2.5
ImageSectionObject 0x020f0268 None \Device\HarddiskVolume1\WINDOWS\svchost.exe
然后我们strings一下看看
# lightless @ lightless-pc in ~/Desktop/seccon2016/volatility_2.5.linux.standalone/output [22:16:33]
$ cat file.None.0x81efa390.img | strings
!This program cannot be run in DOS mode.
fRich;
.text
...
Press <CTRL>+Break to PAUSE, <CTRL>+C to RESUME and close window to STOP
Main - WinExec running
C:\Program Files\Internet Explorer\iexplore.exe http://crattack.tistory.com/entry/Data-Science-import-pandas-as-pd
Main - run
Main - stop
...
找到了一个URL,访问后并没有什么特别的,那么看一下hosts文件。
# lightless @ lightless-pc in ~/Desktop/seccon2016/volatility_2.5.linux.standalone [22:19:22]
$ ./volatility_2.5_linux_x64 -f ../forensic_100.raw filescan | grep hosts
Volatility Foundation Volatility Framework 2.5
0x000000000217b748 1 0 R--rw- \Device\HarddiskVolume1\WINDOWS\system32\drivers\etc\hosts
# lightless @ lightless-pc in ~/Desktop/seccon2016/volatility_2.5.linux.standalone [22:19:28]
$ ./volatility_2.5_linux_x64 -f ../forensic_100.raw dumpfiles -D output -Q 0x000000000217b748
Volatility Foundation Volatility Framework 2.5
DataSectionObject 0x0217b748 None \Device\HarddiskVolume1\WINDOWS\system32\drivers\etc\hosts
# lightless @ lightless-pc in ~/Desktop/seccon2016/volatility_2.5.linux.standalone [22:19:35]
$ cat output/file.None.0x819a3008.dat
# Copyright (c) 1993-1999 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
127.0.0.1 localhost
153.127.200.178 crattack.tistory.com %
果然被绑了hosts,我们也绑上hosts再访问一下看看
# lightless @ lightless-pc in ~/Desktop/seccon2016/volatility_2.5.linux.standalone [22:19:44]
$ curl http://crattack.tistory.com/entry/Data-Science-import-pandas-as-pd
SECCON{_h3110_w3_h4ve_fun_w4rg4m3_}
取证300
题目给了一个qcow2的文件。
先把这东西转成raw disk看看
# lightless @ lightless-pc in ~/Desktop/seccon2016 [22:27:28]
$ qemu-img convert disk.qcow2 disk.raw
# lightless @ lightless-pc in ~/Desktop/seccon2016 [22:27:59]
$ fdisk disk.raw -l
Disk disk.raw: 1 GiB, 1073741824 bytes, 2097152 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: dos
Disk identifier: 0x00000000
估计是分区表坏了,用TestDisk修下试试
# lightless @ lightless-pc in ~/Desktop/seccon2016 [22:31:41]
$ fdisk disk.raw -l
Disk disk.raw: 1 GiB, 1073741824 bytes, 2097152 sectors
Units: sectors of 1 * 512 = 512 bytes
Sector size (logical/physical): 512 bytes / 512 bytes
I/O size (minimum/optimal): 512 bytes / 512 bytes
Disklabel type: dos
Disk identifier: 0x00000000
Device Boot Start End Sectors Size Id Type
disk.raw1 * 63 2088449 2088387 1019.7M b W95 FAT32
可以识别出来了,那么继续把disk挂载上
# lightless @ lightless-pc in ~/Desktop/seccon2016 [22:33:45] C:1
$ sudo mount -t vfat -o offset=32256,ro disk.raw /mnt/seccon
# lightless @ lightless-pc in ~/Desktop/seccon2016 [22:33:51]
$ cd /mnt/seccon
# lightless @ lightless-pc in /mnt/seccon [22:33:56]
$ ls
ldlinux.c32 ldlinux.sys syslinux.cfg tce
offset设置为32256的原因是,这个镜像从63扇区开始的,扇区大小是512字节,所以63*512
仔细寻找后会发现有mydata.tgz,复制出来然后解压,可以看到一些敏感的东西
# lightless @ lightless-pc in /tmp/mydata/home/tc [22:37:30]
$ ls -alh
total 248K
drwxr-x--- 9 lightless lightless 4.0K 11月 29 09:57 .
drwxrwxr-x 3 lightless lightless 4.0K 11月 29 09:42 ..
-rw-rw-r-- 1 lightless lightless 233 11月 29 09:57 .ash_history
-rw-r--r-- 1 lightless lightless 446 7月 4 20:00 .ashrc
drwx------ 2 lightless lightless 4.0K 11月 29 09:56 .config
drwx------ 3 lightless lightless 4.0K 11月 29 09:56 .dbus
drwxr-xr-x 2 lightless lightless 4.0K 11月 29 09:56 Desktop
drwx------ 3 lightless lightless 4.0K 11月 29 09:54 .fltk
-rwxr-xr-x 1 lightless lightless 15K 11月 29 09:57 getflag
-rw-r--r-- 1 lightless lightless 169K 11月 29 09:57 h1dd3n_s3cr3t_f14g.jpg
drwxr-x--- 4 lightless lightless 4.0K 11月 29 09:56 .local
drwx------ 4 lightless lightless 4.0K 11月 29 09:56 .mozilla
-rw-r--r-- 1 lightless lightless 920 7月 4 20:00 .profile
-rwxr-xr-x 1 lightless lightless 103 11月 29 09:42 .setbackground
lrwxrwxrwx 1 lightless lightless 20 11月 29 09:54 .wbar -> /usr/local/tce.icons
drwxr-x--- 2 lightless lightless 4.0K 11月 29 09:42 .X.d
-rwxr-xr-x 1 lightless lightless 275 11月 29 09:42 .Xdefaults
-rwxr-xr-x 1 lightless lightless 450 11月 29 09:42 .xsession
本来想直接跑getflag的,但是题目说有马,没敢跑。
把ELF扔到IDA看看。
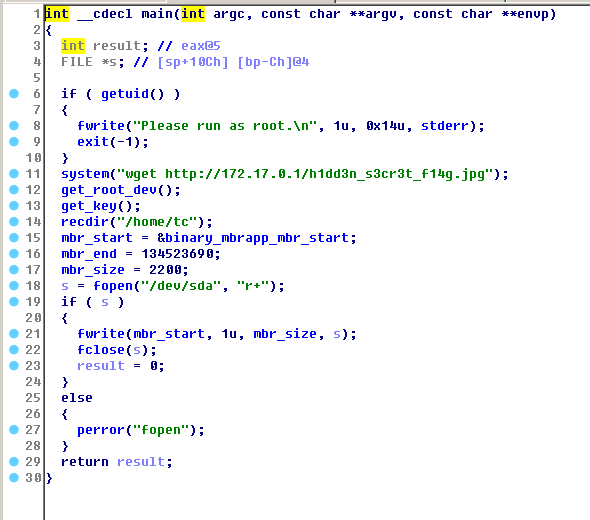
很强啊,先从/dev/urandom读取密钥,然后加密一通,最后连MBR都干掉了,现在只能想办法找到密钥,因为是XOR的加密,还有机会。
找到这个文件:home/tc/.mozilla/firefox/wir5mrmb.default/blocklist.xml
这个是Firefox45里面的,ESR版本,然后把密文和原文比对一下就能找到秘钥了,贴个别人的POC
#!/usr/bin/python3
#
key = [b'\x00']*0x400
enc = open('./home/tc/h1dd3n_s3cr3t_f14g.jpg', 'rb').read()
dec = b''
f2 = 'blocklist.xml'
c2 = open('./home/tc/.mozilla/firefox/wir5mrmb.default/' + f2, 'rb').read()
p2 = open('./firefox/browser/' + f2, 'rb').read()
for i in range(len(key)):
key[i] = bytes([p2[i] ^ c2[i]])
for i in range(len(enc)):
dec += bytes([enc[i] ^ ord(key[i%len(key)])])
open('./f14g_decrypted.jpg', 'wb').write(dec)
打开图片可见flag
SECCON{This is Virtual FAT too}}

[...]11.SECCON2016 取证题 WriteUP[...]
'+(43812*42793)+'